Our cybersecurity framework is above the Essential 8 Australian Government standards for your protection. And our commitment strategy is to Identify, Protect, Detect, Respond and Recover your sensitive information.
Information is fundamental to doing business and data has never been more vulnerable to malicious actors. Our Managed Security Service will take on the responsibility of managing your network, implementing cybersecurity best practices and keeping your data secure.
The key to providing comprehensive cybersecurity is knowing your network and processes and identify all potential risk factors. From there, a strategy is put in place to protect and monitor your sensitive information.
The best way to negate threats is to consult the experts; our Managed Security staff have more than experience, they are accredited experts.
INDENTIFY
LOOKUP’S Security Operations Centre identifies the cyber security risk to your organisation and its people, systems, assets, data and capabilities. This is completed through cyber security risk assessments and vulnerability scanning.
PROTECT
LOOKUP implements appropriate safeguards to ensure the delivery and Protection of the critical services identified. This is managed through Conditional Access, Multi-factor authentication, SOPHOS Synchronised Security, Microsoft Advanced Threat Protection, and Security & Awareness Training.
DECTECT
Detection measures are implemented which assist in identifying the occurrence of a cyber security event. These include SOPHOS Alerts, DarkWebID Alerts and Microsoft Azure/Quarantine centre alerts. Additionally, with staff security training, users themselves become an alerted to Phishing Attacks & Social Engineering.
RESPOND
The LOOKUP SOC team Responds with a preliminary investigation to determine the legitimacy and scope of the alert.
RECOVER
A Recovery plan is actioned to bring the system, account or device back to a baseline protection state. Information obtained during this entire process is fed back into our framework, which then evolves subsequent protection, detection, response and recovery processes in turn.
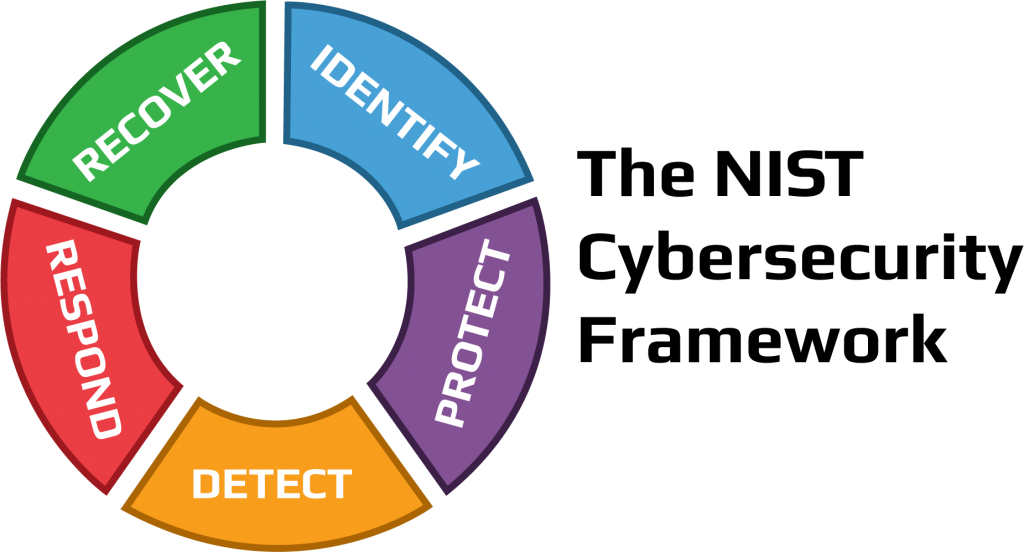
The NIST Cybersecurity Framework is a set of best practices, standards, and recommendations that help an organization improve its cybersecurity measures. Learn more by downloading the PDF below.
